After analysing the Question Paper, it can be concluded that the examiner has tested the knowledge of the basics, understanding of applications of science in real life and the current issues related to the scientific field
There were 14 Questions from Science & Technology in 2022, of which
- 2 Questions from Bio-Technology (Vaccines, DNA barcoding)
- 5 Questions from Computing (open-source digital platforms, Web 3-0, SaaS, qubit, NFTs)
- 2 Questions from Physics (Solar Flare, Communication Technology)
- 1 Question from Chemistry (Nanoparticle)
- 1 Question from Defence (Fractional Orbital Bombardment)
- 3 Questions from Biology (Bacteria, Probiotics, Lymphocytes)
The level of the questions was moderate to tough.
Most of the questions were aimed at testing knowledge of the basics.
Solved PYQs Science & Technology With Explanation 2022 UPSC Prelims (Previous Year Questions)
1. Consider the following:
1. Aarogya Setu
2. CoWIN
3. Digi Locker
4. DIKSHA
Which of the above are built on top of open-source digital platforms?
(a) 1 and 2 only
(b) 2, 3 and 4 only
(c) 1, 3 and 4 only
(d) 1, 2, 3 and 4
1. Ans: d
Explanation:
A Digital Platform is a business-driven framework that allows a community of partners, providers and consumers to share, extend or enhance digital processes and capabilities for the benefit of all stakeholders involved through a common digital technology system.
Closed source software – The creator or copyright holder sells the proprietary or closed source software to end users, who are not allowed to edit, enhance or redistribute the product except as specified by the copyright holder. Ex- software applications such as Microsoft Word or Adobe Illustrator.
Open source software (OSS) is source code developed and maintained through open collaboration. Anyone can use, examine, alter and redistribute OSS as they see fit, typically at no cost.
“Open source” also refers to a community-based approach to creating intellectual property, such as software, through open collaboration, inclusiveness, transparency and frequent public updates.
Examples of open source – GitHub, Mozilla Firefox, Linux, WordPress, Bitcoin, and Android.
About Digilocker
- DigiLocker is a secure cloud based platform for storage, sharing and verification of documents & certificates.
- DigiLocker system is developed on an Open Source stack and the components in its entirety or in parts may be made available to other countries for their own implementation of a similar product.
- Utilization of cloud based services by DigiLocker for secure and scalable system can be good best practise to be replicated globally.
About Aarogya Setu
- On 2nd April 2020, India launched Aarogya Setu mobile App for helping augment the efforts of limiting the spread of COVID19, with an objective of enabling Bluetooth based contact tracing, mapping of likely hotspots and dissemination of relevant information about COVID19. The key pillars of Aarogya Setu have been transparency, privacy and security and in line with India’s policy on Open Source Software, the source code of Aarogya Setu has now been made open source.
About DIKSHA
- DIKSHA (Digital Infrastructure for Knowledge Sharing) is a national platform for school education, an initiative of National Council for Educational Research and Training (NCERT), under the aegis of the Ministry of Education (MoE), GoI.
- DIKSHA is built on open source technology, made in India and made for India, which incorporates internet scale technologies and enables several use-cases and solutions for teaching and learning. DIKSHA is built using MIT licensed open source technology called Sunbird, which is a digital infrastructure for learning and solutions and offers over a 100 micro services as building blocks for the development of platforms and solutions.
About COWIN
- CoWin stands for Covid Vaccine Intelligent Work. In January 2021, the platform was unveiled by the union government as it launched the vaccination drive in the country.
- The primary feature is to give users a chance to book a vaccine slot anywhere in the country
- The code for CoWin was made open source. The government won’t attach any intellectual property rights to it.
Hence, option d is correct.
2. With reference to Web 3-0, consider the following statements:
1. Web 3-0 technology enables people to control their own data.
2. In Web 3-0 world, there can be blockchain-based social networks.
3. Web 3-0 is operated by users collectively rather than a corporation.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
2. Ans: d
Explanation:
Web3 is the third generation of the internet currently being built, where websites and apps will be able to process information in a smart human-like way through technologies like artificial intelligence (AI), machine learning (ML), Big Data, decentralized ledger technology (DLT), and more.
Web3 was in fact originally called the Semantic Web by World Wide Web inventor Tim Berners-Lee, and was aimed at being a more autonomous, intelligent, and open internet.
In Web3, data will be interconnected in a decentralised way, where as in Web 2.0, data is mostly stored in centralised repositories and therefore subject to manipulation or worse. Furthermore, users and machines will be able to interact with data.
Web3 networks will operate through decentralised protocols — the founding blocks of blockchain and cryptocurrency technology.
Hence, statements 1, 2 and 3 are correct.
3. With reference to “Software as a Service (SaaS)”, consider the following statements
1. SaaS buyers can customise the user interface and can change data fields.
2. SaaS users can access their data through their mobile devices.
3. Outlook, Hotmail and Yahoo! Mail are forms of SaaS.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
3. Ans: d
Explanation:
Software as a service (SaaS) is application software hosted on the cloud and used over an internet connection by way of a web browser, mobile app or thin client.
Software as a service (SaaS) allows users to connect to and use cloud-based apps over the Internet. Common examples are email, calendaring, and office tools (such as Microsoft Office 365).
SaaS provides a complete software solution that you purchase on a pay-as-you-go basis from a cloud service provider. You rent the use of an app for your organization, and your users connect to it over the Internet, usually with a web browser.
All of the underlying infrastructure, middleware, app software, and app data are located in the service provider’s data center.
The service provider manages the hardware and software, and with the appropriate service agreement, will ensure the availability and the security of the app and your data as well.
SaaS allows your organization to get quickly up and running with an app at minimal upfront cost.
Common SaaS scenarios
Web-based email service such as Outlook, Hotmail, or Yahoo! Mail
With these services, you log into your account over the Internet, often from a web browser. The email software is located on the service provider’s network, and your messages are stored there as well.
You can access your email and stored messages from a web browser on any computer or Internet-connected device.
Hence, statement 3 is correct.
Advantages of SaaS
- Gain access to sophisticated applications. To provide SaaS apps to users, you don’t need to purchase, install, update, or maintain any hardware, middleware, or software. SaaS makes even sophisticated enterprise applications, such as ERP and CRM, affordable for organisations that lack the resources to buy, deploy, and manage the required infrastructure and software themselves.
- Pay only for what you use. You also save money because the SaaS service automatically scales up and down according to the level of usage.
- Use free client software. Users can run most SaaS apps directly from their web browser without needing to download and install any software, although some apps require plugins. This means that you don’t need to purchase and install special software for your users.
- Access app data from anywhere. With data stored in the cloud, users can access their information from any Internet-connected computer or mobile device. And when app data is stored in the cloud, no data is lost if a user’s computer or device fails.
Hence, statement 2 is correct.
- Customization and integration. SaaS services enable deep customization so apps can be configured specifically to each customer’s requirements, including the functionality and look-and-feel of the product. Such systems can also be integrated with other business apps, especially across applications from a common software provider.
Hence, statement 1 is correct.
- Data and analytics. With a SaaS application, all processes, data and files are carried out through a centralized platform, making it easy to collect, store and analyze data further, even for distributed teams.
4. Which one of the following statements best reflects the idea behind the “Fractional Orbital Bombardment System” often talked about in media?
(a) A hypersonic missile is launched into space to counter the asteroid approaching the Earth and explode it in space.
(b) A spacecraft lands on another planet, after making several orbital motions.
(c) A missile is put into a stable orbit around the Earth and de-orbits over a target on the Earth.
(d) A spacecraft moves along a comet with the same speed and places a probe on its surface.
4. Ans: c
Explanation:
Fractional orbital bombardment systems (FOBS) is a term coined by the West during the Cold War for a Soviet innovation that would exploit limitations in the US Ballistic Missile Early Warming (BMEW) radar system at that time.
The concept of the FOBS was to insert a thermonuclear warhead into a steeply inclined low altitude polar orbit, such that it would approach the continental United States (CONUS) from any direction, but primarily from the southern hemisphere.
The idea behind FOBS is, a warhead is put into a stable orbit and it deorbits over the target. The warhead would employ retrorockets to break itself out of orbit and fall on the target from a direction not covered by BMEW.
The FOB system is distinguished from an ICBM delivery system in that an ICBM take a ballistic trajectory that reaches an altitude of approximately 800 miles (1,300 kilometers) and releases its warhead or warhead bus, which then descends on a ballistic trajectory to its target
A FOBS trajectory launches a warhead and its delivery vehicle into an orbit of around 100 miles (160 kilometers) but breaks from that orbit before it completes a full revolution of the Earth.
FOBS , ICBM &MOBS
The FOB system is distinguished from an ICBM delivery system in that an ICBM take a ballistic trajectory that reaches an altitude of approximately 800 miles (1,300 kilometers) and releases its warhead or warhead bus, which then descends on a ballistic trajectory to its
Another concept explored by the Soviet Union was the multiple orbit bombardment system (MOBS), also called the nuclear-armed bombardment system (NABS), where a vehicle carrying either a single or several warheads would make one or more complete orbits of the Earth before it delivered its payload. MOBS are differentiated from FOBS in as their weapons complete one or more orbits before descending on its target.
A fractional orbital bombardment system has several advantages over traditional ballistic missiles: its range covers the entire Earth; it can execute an attack from a much larger number of directions; and the time required for payload delivery can be many minutes shorter than for a comparable ICBM payload.
Fractional orbital bombardment systems are inaccurate delivery mechanisms. The large velocity of the payload during re-entry and subsequent delivery creates a significant degree of error in targeting.
Unlike error-prone bombardment systems, a hypersonic glide vehicle can maneuver and adjust its flight path precisely after re-entry into the atmosphere. It can sustain atmospheric flight for an extended period (a “glide”), or even exit and re-enter the atmosphere later (a “skip”). Non-ballistic atmospheric entry enables hypersonic glide vehicles to avoid interception by following unpredictable flight paths, and to fly below the ceilings of radar detection systems.
A fractional orbital hypersonic delivery system combines these advantages with orbital bombardment to create the best of both worlds. A fractional orbital hypersonic delivery system can deliver payloads up to 10 minutes faster than ICBMs. The trajectories of fractional orbital hypersonic delivery systems are difficult to track, both because they stay closer to the Earth and therefore below the floor of missile-defense radars, and also because of the increased manoeuvrability of the hypersonic glide vehicle payload.
Hence, option c is correct.
5. Which one of the following is the context in which the term “qubit” is mentioned?
(a) Cloud Services
(b) Quantum Computing
(c) Visible Light Communication Technologies
(d) Wireless Communication Technologies
5. Ans: b
Explanation:
What is quantum?
The quantum in “quantum computing” refers to the quantum mechanics that the system uses to calculate outputs. In physics, a quantum is the smallest possible discrete unit of any physical property. It usually refers to properties of atomic or subatomic particles, such as electrons, neutrinos, and photons.
What is a qubit?
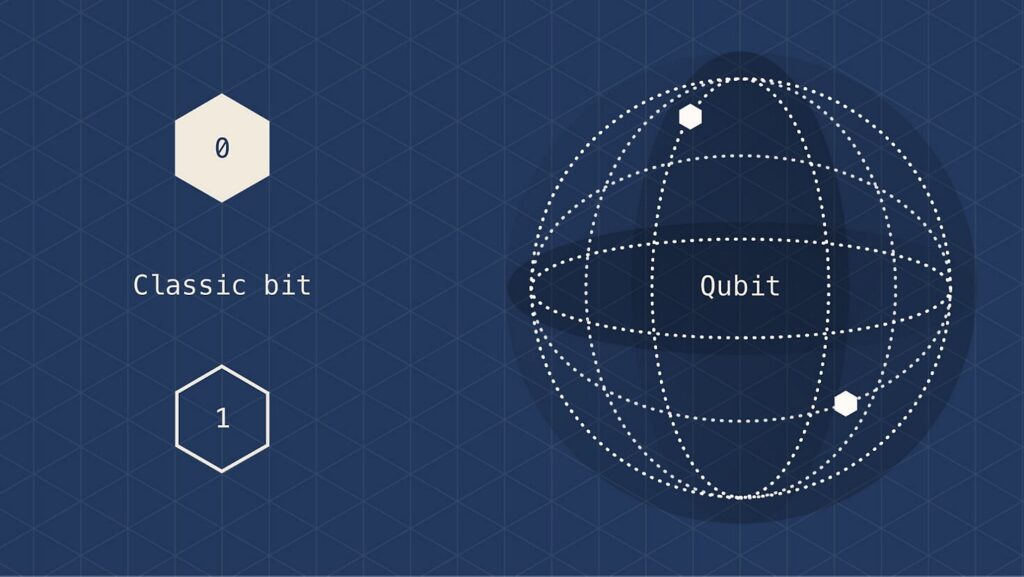
A qubit is the basic unit of information in quantum computing. Qubits play a similar role in quantum computing as bits play in classical computing, but they behave very differently. Classical bits are binary and can hold only a position of 0 or 1, but qubits can hold a superposition of all possible states.
What is quantum computing?
Quantum computers harness the unique behavior of quantum physics—such as superposition, entanglement, and quantum interference—and apply it to computing. This introduces new concepts to traditional programming methods.
Qubit vs bit
Qubits are represented by a superposition of multiple possible states
A qubit uses the quantum mechanical phenomena of superposition to achieve a linear combination of two states. A classical binary bit can only represent a single binary value, such as 0 or 1, meaning that it can only be in one of two possible states. A qubit, however, can represent a 0, a 1, or any proportion of 0 and 1 in superposition of both states, with a certain probability of being a 0 and a certain probability of being a 1.
In superposition, quantum particles are a combination of all possible states. They fluctuate until they’re observed and measured. One way to picture the difference between binary position and superposition is to imagine a coin. Classical bits are measured by “flipping the coin” and getting heads or tails. However, if you were able to look at a coin and see both heads and tails at the same time, as well as every state in between, the coin would be in superposition.
Superposition gives quantum computers superior computing power
Superposition allows quantum algorithms to process information in a fraction of the time it would take even the fastest classical systems to solve certain problems.
- The amount of information a qubit system can represent grows exponentially. Information that 500 qubits can easily represent would not be possible with even more than 2^500 classical bits.
- It would take a classical computer millions of years to find the prime factors of a 2,048-bit number. Qubits could perform the calculation in just minutes.
Hence, option b is correct.
6. Consider the following communication technologies:
1. Closed-circuit Television
2. Radio Frequency Identification
3. Wireless Local Area Network
Which of the above are considered Short-Range devices/technologies?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
6. Ans: d
Explanation:
Wireless devices that transmit low power levels and operate over distances of up to a few hundred meters are Short Range Devices (SRD). They mostly use Radio frequencies to operate in a small area. Short range communications as the systems providing wireless connectivity within a local sphere of interaction.
Short Range Devices (SRD) are radio devices that offer a low risk of interference with other radio services, usually because their transmitted power, and hence their range, is low. The definition ‘Short Range Device’ may be applied to many different types of wireless equipment, including various forms of:
- Access control (including door and gate openers)
- Alarms and movement detectors
- Closed-circuit television (CCTV)
- Cordless audio devices, including wireless microphones
- Industrial control
- Local Area Networks
- Medical implants
- Metering devices
- Remote control
- Radio frequency identification (RFID)
- Road Transport Telematics
- Telemetry.
They have a low effective radiated power (ERP) of typically 25-100 mW and thus do not interfere with other radio services. The frequencies used by these devices are called SRD frequencies. Other SRD wireless technologies include Bluetooth, Wi-Fi, near-field communication (NFC), ultra-wideband (UWB).
Hence, option d is correct.
7. Consider the following statements:
1. Biofilms can form on medical implants within human tissues.
2. Biofilms can form on food and food processing surfaces.
3. Biofilms can exhibit antibiotic resistance.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
7. Ans: d
Explanation:
Bacteria often attach to surfaces and form dense aggregations called biofilms or bacterial mats. These films can range from a few micrometers in thickness to up to half a meter in depth, and may contain multiple species of bacteria, protists, and achaea.
Bacteria living in biofilms display a complex arrangement of cells and extracellular components, forming secondary structures such as microcolonies through which there are networks of channels to enable better diffusion of nutrients.
In natural environments, such as soil or the surfaces of plants, most bacteria are bound to surfaces in biofilms.
Biofilms are also important in medicine, as these structures are often present during chronic bacterial infections or in infections of implanted medical devices, and bacteria protected within biofilms are much harder to kill than individual isolated bacteria. Even more complex morphological changes are sometimes possible.
Hence, statement 1 is correct.
Biofilms is technically bacteria and exhibits all characteristics of bacteria including attaching to the food surfaces and antibiotic resistance.
Hence, statements 2 and 3 are correct.
8. Consider the following statements in respect of probiotics:
1. Probiotics are made of both bacteria and yeast.
2. The organisms in probiotics are found in foods we ingest but they do not naturally occur in our gut.
3. Probiotics help in the digestion of milk sugars.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 only
(c) 1 and 3
(d) 2 and 3
8. Ans: c
Explanation:
What are probiotics?
Probiotics are live microorganisms that are intended to have health benefits when consumed or applied to the body. They can be found in yogurt and other fermented foods, dietary supplements, and beauty products.
Although people often think of bacteria and other microorganisms as harmful “germs,” many are actually helpful. Some bacteria help digest food, destroy disease-causing cells, or produce vitamins. Many of the microorganisms in probiotic products are the same as or similar to microorganisms that naturally live in our bodies (It is also found it Gut).
Hence, statement 2 is incorrect.
What types of bacteria are in probiotics?
Probiotics may contain a variety of microorganisms. The most common are bacteria that belong to groups called Lactobacillus and Bifidobacterium. Other bacteria may also be used as probiotics, and so may yeasts such as Saccharomyces boulardii. Different types of probiotics may have different effects.
Hence, statement 1 is correct.
Fermentation of milk by lactobacillus bacteria in gut converts lactose sugar of milk into glucose and galactose, which is easily digestible by even the lactose-intolerant. Therefore, probiotics helps in digestion of milk sugars.
Hence, statement 3 is correct.
9. In the context of vaccines manufactured to prevent COVID-19 pandemic, consider the following statements:
1. The Serum Institute of India produced COVID-19 vaccine named Covishield using mRNA platform.
2. Sputnik V vaccine is manufactured using vector based platform.
3. COVAXIN is an inactivated pathogen based vaccine.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
9. Ans: b
Explanation:
About Vaccines
- A vaccine is a biological preparation that improves immunity to a specific disease. It typically contains an agent that resembles a disease-causing microorganism and is often made from weakened or killed forms of the microbe. The agent stimulates the body’s immune system to recognize the agent as foreign, destroy it, and “remember” it so that the immune system can more easily recognize and destroy any of these microorganisms that it later encounters.
- vaccines are administered prior to infection. Their role is to prime the immune system to fight any future infections, so that they can be brought under control before the disease-causing microorganism have had a chance to multiply.
- Vaccines are of different types – killed Vaccines , attenuated Vaccines , toxoid Vaccines, subunit Vaccines, Conjugate Vaccines, experimental Vaccines , Valence Vaccines.
The different types of vaccines
There are three main approaches to designing a vaccine. Their differences lie in whether they use a whole virus or bacterium; just the parts of the germ that triggers the immune system; or just the genetic material that provides the instructions for making specific proteins and not the whole virus.
1. The whole-microbe approach
- Inactivated vaccine
- Live-attenuated vaccine
- Viral vector vaccine
1. Live-attenuated vaccines:
- Live-attenuated vaccines contain live pathogens from either a bacteria or a virus that have been attenuated or weakened.
- They are produced by selecting strains of a bacteria or virus that still produce a robust enough immune response but that does not cause disease.
- Attenuated viruses were one of the earliest methods of eliciting protective immune responses.
- Examples: Measles, mumps, and rubella (MMR) vaccine, varicella (chickenpox) vaccine.
2. Inactivated vaccines
- Inactivated vaccines take a live pathogen and inactivate or kill it. Then the vaccine is introduced to a human through a shot, the inactivated pathogen is strong enough to create an immune response, however, is incapable of causing disease.
- Examples: Polio vaccine, influenza vaccine, Covaxin.
Hence Statement 3 is correct.
3. Viral vector vaccines:
- Viral vector vaccines use a harmless virus to deliver to the host cells the genetic code of the antigen that one wants the immune system to fight against. Viral vectors are a gene delivery system, where information about the antigen is delivered, which triggers the body’s immune response.
- Examples: Ebola vaccine, COVID-19 vaccine (AstraZeneca and Johnson & Johnson), Covishield, Sputnik-V.
2. The subunit approach
A subunit vaccine is one that only uses the very specific parts (the subunits) of a virus or bacterium that the immune system needs to recognize. It doesn’t contain the whole microbe or use a safe virus as a vector. The subunits may be proteins or sugars ( polysaccharides), conjugate. Most of the vaccines on the childhood schedule are subunit vaccines, protecting people from diseases such as whooping cough, tetanus, diphtheria and meningococcal meningitis.
3. The genetic approach (nucleic acid vaccine)
Unlike vaccine approaches that use either a weakened or dead whole microbe or parts of one, a nucleic acid vaccine just uses a section of genetic material that provides the instructions for specific proteins, not the whole microbe. DNA and RNA are the instructions our cells use to make proteins. In our cells, DNA is first turned into messenger RNA, which is then used as the blueprint to make specific proteins example of mRNA vaccines are Comirnaty (Pfizer-BioNTech) and Spikevax (Moderna).
Hence statement 1 is incorrect & statement 2 is correct.
10. If a major solar storm (solar-flare) reaches the Earth, which of the following are the possible effects on the Earth?
1. GPS and navigation systems could fail.
2. Tsunamis could occur at equatorial regions.
3. Power grids could be damaged.
4. Intense auroras could occur over much of the Earth.
5. Forest fires could take place over much of the planet.
6. Orbits of the satellites could be disturbed.
7. Shortwave radio communication of the aircraft flying over Polar Regions could be interrupted.
Select the correct answer using the code given below:
(a) 1, 2, 4 and 5 only
(b) 2, 3, 5, 6 and 7 only
(c) 1, 3, 4, 6 and 7 only
(d) 1, 2, 3,4, 5, 6 and 7
10. Ans: c
Explanation:
What is a solar flare?
A solar flare is an intense burst of radiation, or light, on the Sun. Flares are our solar system’s most powerful explosive events – the most powerful flares have the energy equivalent of a billion hydrogen bombs, enough energy to power the whole world for 20,000 years.
How do solar flares affect Earth?
Solar flares only affect Earth when they occur on the side of the Sun facing Earth. Solar flares are rated into different classes based on their strength, or energy output, and the effect a flare will have on Earth depends on what class it is (B, C, M, and X classes, with X being the most intense).
The most dangerous emissions from flares are energetic charged particles (primarily high-energy protons) and electromagnetic radiation (primarily x-rays).
How does a solar storm affect us?
When directed toward Earth, a solar storm can create a major disturbance in Earth’s magnetic field, called a geomagnetic storm, that can produce effects such as radio blackouts, power outages, and beautiful auroras.
- The x-rays from flares are stopped by our atmosphere well above the Earth’s surface. They do disturb the Earth’s ionosphere, however, which in turn disturbs radio communications.
- X rays along with energetic ultraviolet radiation, they heat the Earth’s outer atmosphere, causing it to expand. This increases the drag on Earth-orbiting satellites, reducing their lifetime in orbit. Also, both intense radio emission from flares and changes in the atmosphere can degrade satellite communications, for example the precision of Global Positioning System (GPS) measurements can be degraded. This might cause an internet outage, meaning an internet shutdown.
Hence, statement 1 is correct.
- One serious problem that can occur during a geomagnetic storm is damage to Earth-orbiting satellites, especially those in high, geosynchronous orbits. Communications satellites are generally in these high orbits. Either the satellite becomes highly charged during the storm and a component is damaged by the high current that discharges into the satellite, or a component is damaged by high-energy particles that penetrate the satellite.
- Currently astronauts are not in immediate danger because they stay relatively near the Earth in low earth orbit. They do have to be concerned about cumulative radiation exposure during space walks.
- The energetic particles from a flare or CME would be dangerous to an astronaut on a mission to the Moon or Mars, however.
- Solar storms, which are much more terrifying near the sun than on Earth, don’t directly cause tsunamis on Earth. Regular tectonic activity continues regardless of solar wind activity.
Hence, statement 2 is incorrect.
- Another major problem that has occurred during geomagnetic storms has been the temporary loss of electrical power over a large region. The best known case of this occurred in 1989 in Quebec. High currents in the magnetosphere induce high currents in power lines, blowing out electric transformers and power stations. This is most likely to happen at high latitudes, where the induced currents are greatest, and in regions having long power lines and where the ground is poorly conducting. The damage to satellites and power grids can be very expensive and disruptive.
Hence, statement 3 is correct.
- One spectacular side-effect of increased solar activity during the solar cycle is aurora. When the energetic particles from the sun slam into Earth’s atmosphere, dazzling light illuminates the sky. The color of the aurora depends on what chemicals in Earth’s atmosphere the particles hit. Red hues are produced from collisions with nitrogen molecules and green is produced by oxygen molecules.
Hence, statement 4 is correct.
- Solar flares produce high energy particles and radiation that are dangerous to living organisms. However, on the surface of the Earth, we are well protected from the effects of solar flares by the Earth’s magnetic field and atmosphere .Forest fires are not caused by solar storms. The flares are not strong till they reach the Earth so as to cause forest fires.
Hence, statement 5 is incorrect.
- When the solar cycle is at peak activity, it can pose a risk to communications on Earth and satellites. It can disturb the orbits of such satellites. The solar storm can endanger astronauts and Earth-orbiting spacecraft.
Hence, statement 6 is correct.
- Shortwave radio communication of the aircraft flying over Polar Regions could also be interrupted by the solar storms as the electronic equipments may malfunction.
Hence, statement 7 is correct.
11. With reference to Non-Fungible Tokens (NFTs), consider the following statements.
1. They enable the digital representation of physical assets.
2. They are unique cryptographic tokens that exist on a blockchain.
3. They can be traded or exchanged at equivalency and therefore can be used as a medium of commercial transactions.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
11. Ans: a
Explanation:
An NFT or non-fungible token is a unique digital asset stored on the blockchain that serves as proof of ownership or authenticity for a digital or physical item/right.
Unlike fungible assets, NFTs are one-of-a-kind and cannot be replaced. They use blockchain technology to provide decentralized, secure, and transparent records of ownership and transfers.
Hence Statement 1& 2 are correct.
There is a close link between NFTs and cryptocurrencies as many NFTs are traded in cryptocurrencies and the fortunes of NFTs have tracked the performance of crypto as well as broader economic trends.
Fundamentally, NFTs are digital certificates that hold the potential to deliver significant value for both organizations and end users. For companies, NFTs provide a new way to connect with customers and create loyal communities. For users, they provide a new avenue for inclusive ownership in digital goods.
NFTs are non-fungible, meaning each token has unique properties and isn’t worth the same amount as similar tokens. Art and collectibles are often considered non-fungible since only one original exists.
Hence Statement 3 is incorrect.
12. Which one of the following statements best describes the role of B cells and T cells in the human body?
(a) They protect the body from environmental allergens.
(b) They alleviate the body’s pain and inflammation.
(c) They act as immunosuppressants in the body.
(d) They protect the body from the diseases caused by pathogens.
12. Ans: d
Explanation:
Blood Basics
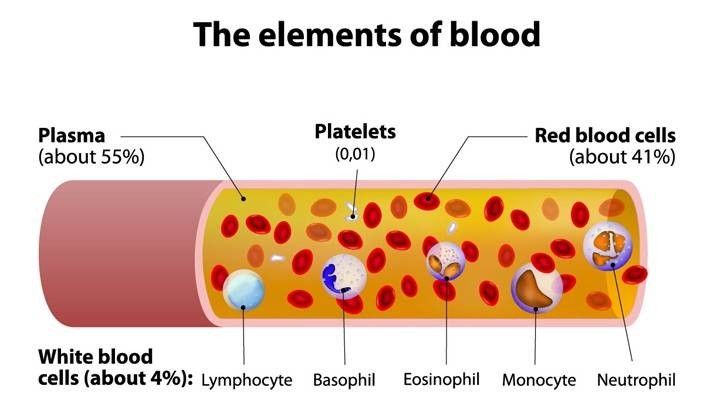
Blood is a specialized body fluid. It has four main components: plasma, red blood cells, white blood cells, and platelets.
The Components of Blood and Their Importance
1. Plasma
The liquid component of blood is called plasma, a mixture of water, sugar, fat, protein, and salts. The main job of the plasma is to transport blood cells throughout your body along with nutrients, waste products, antibodies, clotting proteins, chemical messengers such as hormones, and proteins that help maintain the body’s fluid balance.
2. Red Blood Cells (also called erythrocytes or RBCs)
Known for their bright red color, red cells are the most abundant cell in the blood, accounting for about 40 to 45 percent of its volume.
Production of red blood cells is controlled by erythropoietin, a hormone produced primarily by the kidneys.
Red blood cells start as immature cells in the bone marrow and after approximately seven days of maturation are released into the bloodstream. The red blood cell survives on average only 120 days.
Red cells contain a special protein called hemoglobin, which helps carry oxygen from the lungs to the rest of the body and then returns carbon dioxide from the body to the lungs so it can be exhaled. Blood appears red because of the large number of red blood cells, which get their color from the hemoglobin.
3. White Blood Cells (also called leukocytes)
White blood cells protect the body from infection. They are much fewer in number than red blood cells, accounting for about 1 percent of blood.
There are different types of white blood cells
a. Lymphocyte :The other major type of white blood cell is a lymphocyte. Lymphocytes make antibodies to fight infection. They are found in the lymph nodes, thymus, spleen, tonsils, adenoids and bone marrow. They are also found in lymphatic tissue in other parts of the body, such as the appendix, the small intestine and other parts of the digestive system and respiratory system.
There are two main populations of these cells.
T lymphocytes help regulate the function of other immune cells and directly attack various infected cells and tumors.
B lymphocytes make antibodies, which are proteins that specifically target bacteria, viruses, and other foreign materials.
b. Granulocytes :Granulocytes fight infection and become active in response to tissue inflammation.
The 3 main types of granulocytes are: Neutrophils, Eosinophils and Basophils
Neutrophils : The most common type of white blood cell is the neutrophil, which is the “immediate response” cell and accounts for 55 to 70 percent of the total white blood cell count.
Each neutrophil lives less than a day, so bone marrow must constantly make new neutrophils to maintain protection against infection.
Eosinophils and Basophils, which attack and destroy certain parasites and are activated during an allergic reaction
c. Monocytes : Monocytes help fight infection by changing into cells called macrophages, which eat foreign invaders, such as bacteria and waste from dying cells.
4.Platelets (also called thrombocytes)
Unlike red and white blood cells, platelets are not actually cells but rather small fragments of cells. Platelets help the blood clotting process (or coagulation) by gathering at the site of an injury, sticking to the lining of the injured blood vessel, and forming a platform on which blood coagulation can occur.
A higher than normal number of platelets can cause unnecessary clotting, which can lead to strokes and heart attacks , Conversely, lower than normal counts can lead to extensive bleeding.
Where Do Blood Cells Come From?
Blood cells develop from hematopoietic stem cells and are formed in the bone marrow through the highly regulated process of hematopoiesis. Hematopoietic stem cells are capable of transforming into red blood cells, white blood cells, and platelets.
Stem cells are found in the bone marrow, blood and umbilical cord blood. Stem cells develop into blood cells in the bone marrow. When blood cells are mature and able to function, they leave the bone marrow and move into the blood.
Most stem cells are found in the bone marrow. Stem cells can also be found in smaller amounts in the bloodstream. These are called peripheral blood stem cells. Umbilical cord blood also has stem cells but there are fewer stem cells than those in the bone marrow and blood.
These stem cells can be found circulating in the blood and bone marrow in people of all ages, as well as in the umbilical cords of newborn babies. Stem cells from all three sources may be used to treat a variety of diseases, including leukemia, lymphoma, bone marrow failure, and various immune disorders.
Hence, option d is correct.
13. Consider the following statements:
DNA Bar-coding can be a tool to:
1. assess the age of a plant or animal.
2. distinguish among species that look alike.
3. identify undesirable animal or plant materials in processed foods.
Which of the statements given above is/are correct?
(a) 1 only
(b) 3 only
(c) 1 and 2
(d) 2 and 3
13. Ans: d
Explanation:
What Is DNA Barcoding
DNA barcoding is a method used to identify specimens through short, standardized segments of DNA. Each species has its own unique barcode, much like how every person has a distinct fingerprint. These DNA barcodes can be compared to a reference library, allowing for accurate identification of the species.
The DNA sequence helps identify different species, similar to how a supermarket scanner uses the black stripes of a UPC barcode to recognize purchases.
DNA barcoding helps identify unknown specimens by matching a specific section of their DNA, known as a barcode, with a reference database that contains DNA from known species.
Comparison to reference databases enables matching unknown samples to known species’ barcodes, allowing fast taxonomic identification.
DNA barcoding is a powerful methodology that employs sequence analysis of standardized genetic regions to quickly and accurately characterize species diversity within intricate biological communities. This approach not only facilitates the identification of known species but also supports the discovery of new species, assists in phylogenetic analyses, and enhances our understanding of evolutionary processes.
The versatility of DNA barcoding has resulted in a wide range of applications across various fields.
In environmental science, it aids in assessing biodiversity, detecting invasive species, identifying agricultural pests and disease vectors, and monitoring ecosystem health.
In industry, DNA barcoding is employed to verify the authenticity of ingredients in food, pharmaceuticals, and other products, as well as for quality control purposes.
Forensic investigators also utilize barcoding to trace the origins of samples and combat wildlife trafficking.
Hence, statements 2 and 3 are correct.
The approximation of age of plants and animals is not done using DNA barcoding. Carbon dating is used to estimate the age of fossils.
Hence, statement 1 is incorrect.
14. Consider the following statements:
1. Other than those made by humans, nanoparticles do not exist in nature.
2. Nanoparticles of some metallic oxides are used in the manufacture of some cosmetics.
3. Nanoparticles of some commercial products which enter the environment are unsafe for humans.
Which of the statements given above is/are correct?
(a) 1 only
(b) 3 only
(c) 1 and 2
(d) 2 and 3
14. Ans: d
Explanation:
Nanoparticles are particles that exist on a nanometre scale (i.e., below 100 nm in at least one dimension). They can possess physical properties such as uniformity, conductance or special optical properties that make them desirable in materials science and biology. Naturally occurring nanoparticles can be found in volcanic ash, ocean spray, fine sand and dust, and even biological matter (e.g. viruses).
Nanoparticles, can have the same dimensions as biological molecules such as proteins. In living systems, they may immediately adsorb onto their surface some of the large molecules they encounter as they enter the tissues and fluids of the body.
Hence, statement 1 is incorrect.
Nanotechnology has revolutionised industry. It is used to improve wide-ranging products, from cosmetics, toys and toothpastes to textiles and missiles. They are important constituents of sunscreen lotions.
Some other uses of nanoparticles:
- Harvesting CO2: To help slow the climate-changing rise in atmospheric CO2 levels, researchers have developed nanoCO2 harvesters that can suck atmospheric carbon dioxide and deploy it for industrial purposes or convert it into useful products like methanol.
- Cleansing Water: Most toxic dyes used in textile and leather industries can be captured with nanoparticles. Appropriately designed magnetic nanomaterials can be used to separate pollutants such as arsenic, lead, chromium and mercury from water. In addition to removing dyes and metals, nanomaterials can also be used to clean up oil spills.
- Nanoparticles can accelerate the anaerobic digestion of the sludge, thus making it more efficient in terms of duration and enhanced production of the biogas.
Hence, statement 2 is correct.
While nanoparticles have potential to solve environmental problems, the small size that makes them useful for environmental cleanup also raises special concerns about health and persistence in the environment.
Key factors in the interaction with living structures include nanoparticle dose, the ability of nanoparticles to spread within the body, as well as their solubility. Some nanoparticles dissolve easily and their effects on living organisms are the same as the effects of the chemical they are made of. However, other nanoparticles do not degrade or dissolve readily. Instead, they may accumulate in biological systems and persist for a long time, which makes such nanoparticles of particular concern.
Nanoparticles accumulate in the environment and kill the beneficial bacteria. Nanoparticles are released into the environment through the products they are used in like nanoparticles of zinc and titanium oxide damage DNA in cell lines, nanotitanium dioxide particles interfere with the genetic functioning of zebrafish embryos.
Hence, statement 3 is correct.



