After a thorough analysis of the 2020 Question Paper, it can be concluded that the examiner has tested varied areas with a focus on the scientific issues which are in the news and on basics.
There were 13 Questions from Science & Technology in 2020, of which
- 3 Questions from Computing (AI, PKI, Block Chain)
- 2 Questions from Genetics (Pronuclear Transfer, Gene Editing)
- 3 Questions from Physics (VLC, Drones, Solar Water Pumps)
- 1 Questions from Energy (IAEA Safeguards)
- 1 Question from Biology (Plant & Animal Cell)
- 1 Question from Chemistry (CNTs)
- 1 Question from Space (Evolved LISA)
- 1 Question from Bio-Technology (Vaccines)
The level of the questions was moderate to tough.
Most of the questions were aimed to test knowledge of the basics and analytical abilities.
Solved PYQs Science & Technology With Explanation 2020 UPSC Prelims (Previous Year Questions)
1. In the context of recent advances in human reproductive technology, “Pronuclear Transfer” is used for:
(a) Fertilisation of egg in vitro by the donor sperm
(b) Genetic modification of sperm producing cells
(c) Development of stem cells into functional embryos
(d) Prevention of mitochondrial diseases in offspring
1. Ans: d
Explanation:
Mitochondrial DNA (mtDNA) mutations are a common cause of genetic disease with pathogenic mtDNA mutations. MtDNA is transmitted maternally only and it has been proposed that nuclear transfer techniques may be an approach to prevent the transmission of human mtDNA disease
Pronuclear transfer program is a reproductive method of transferring the nuclear DNA of a fertilized egg into a donor egg from which nuclea DNA has been removed. This technique is used to prevent maternally inherited mitochondrial DNA abnormalities.
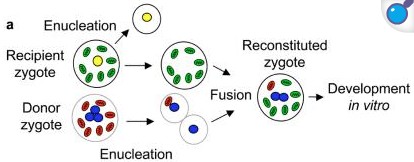
Hence, option d is correct.
2. With the present state of development, Artificial Intelligence can effectively do which of the following?
1. Bring down electricity consumption in industrial units
2. Create meaningful short stories and songs
3. Disease diagnosis
4. Text-to-Speech Conversion
5. Wireless transmission of electrical energy
Select the correct answer using the code given below:
(a) 1, 2, 3 and 5 only
(b) 1, 3 and 4 only
(c) 2, 4 and 5 only
(d) 1, 2, 3, 4 and 5
2. Ans: b
Explanation:
Artificial intelligence is a field of science concerned with building computers and machines that can reason, learn, and act in such a way that would normally require human intelligence or that involves data whose scale exceeds what humans can analyze.
AI is a set of technologies that are based primarily on machine learning and deep learning, used for data analytics, predictions and forecasting, object categorization, natural language processing, recommendations, intelligent data retrieval, and more.
Applications and use cases for artificial intelligence
- Speech recognition: Automatically convert spoken speech into written text.
- Image recognition
- Translation: Translate written or spoken words from one language into another.
- Predictive modeling: Mine data to forecast specific outcomes with high degrees of granularity.
- Data analytics: Find patterns and relationships in data for business intelligence.
- Cybersecurity: Autonomously scan networks for cyber attacks and threats.
- Reduce emission: Reports predict that AI has the potential to help mitigate 5-10% of global GHG emissions by 2030
- Reduce energy demand: Computer chip maker Nvidia claims its new ‘superchip’ can deliver a 30 times performance improvement when running generative AI services, while using 25 times less energy.
- Artificial intelligence techniques ranging from machine learning to deep learning are prevalent in healthcare for disease diagnosis, drug discovery, and patient risk identification.
AI doesn’t have the ability to truly innovate or think creatively— it can only rearrange and analyze existing information.
Hence, statement 2 is incorrect.
Wireless power transmission (WPT)
- It is the efficient transmission of electric power from one point to another through vacuum or an atmosphere without the use of wire or any other substance.
- This can be used for applications where either an instantaneous amount or a continuous delivery of energy is needed, but where conventional wires are unaffordable, inconvenient, expensive, hazardous, unwanted or impossible.
- The power can be transmitted using inductive coupling for short range, resonant induction for mid range and electromagnetic wave power transfer for high range.
- One of the major drawbacks in current power distribution system is the losses during the transmission of electrical energy. As the demands of power are increasingconveniently, power generation also increases and this leads to increase power loss during transmission.
- So, AI is not used in wireless power transmission. Hence Statement 5 is incorrect.
Hence, only statement 1,3 and 4 are correct.
3. With reference to Visible Light Communication (VLC) technology, which of the following statements are correct?
1. VLC uses electromagnetic spectrum wavelengths 375 to 780 nm
2. VLC is known as long-range optical wireless communication.
3. VLC can transmit large amounts of data faster than Bluetooth
4. VLC has no electromagnetic interference
Select the correct answer using the code given below:
(a) 1, 2 and 3 only
(b) 1, 2, and 4 only
(c) 1, 3 and 4 only
(d) 2, 3, and 4 only
3. Ans: c
Explanation:
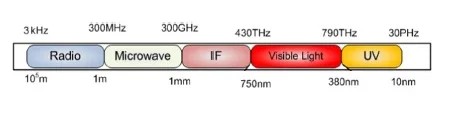
Optical wireless communication (OWC)
Conventional radio frequency (RF) technique which has a regulated and licensed electromagnetic spectrum band, spanning from 30 kHz to 300 GHz. Due to an exponential increase in the wireless data traffic and advanced mobile devices, there are calamities that are emerging within the RF band. This increase leads to spectral crisis such as congestion and maximum data rates that are low relative to OWC. Recent developments and standardization of various RF technologies are not able to overcome these looming crisis
OWC spectral band is between 300 GHz and 30 000 THz (wavelength between 1 mm and 10 nm) of the electromagnetic spectrum, covering the infrared (IR), visible light, and ultraviolet (UV) light bands
OWC technology has an edge over the RF technology due to various factors. These factors include but are not limited to high energy efficiency, widely spread bandwidth which is free from regulation, intrinsic security, and low economical costs.

The categories are briefly explained by giving examples of OWC applications.
- Ultrashort range category (typically about a range of 100 or less), OWC is used for optical communication between and within chips of integrated circuits (ICs).
- Short-range category (typically within a distance of about 1 m), OWC is used to create communication links between the ever-present electronic equipment for daily use. The said equipment form the wireless personal area networks (WPANs). Such networks wirelessly interconnect electronic devices that are used around an individual’s personal work space. Moreover, the short range is used for the establishment of wireless body area networks (WBANs). WBAN is a network, which continually monitors the health of a patient by means of embedding one or more electronic devices within the body or surface mounting the device at a specific body part.
- Medium-range category (typically up to 10 km) is concerned with, but not limited to, indoor infrared and communication within the visible light spectrum band which is commonly known as visible light communication (VLC).
- Long-range category Free-space optical communication (FSO) communication which is also referred to as outdoor intrabuilding links, FSO communication, maximum data transfer rates up to 2.5 Gbps is possible, unlike the maximum data transfer rates of 622Mbps offered by RF communication systems. FSO involves the optical transmission of voice, video, and data using air as the medium of transmission.
- Ultralong range category (typically 4500 km to 10,000 km) is concerned with laser communication in space for intersatellite links.
In RF wireless communication systems, the scramble for spectrum is increasing by a very high magnitude yearly . To complement the conventional RF wireless communication systems is to explore other frequency bands in the electromagnetic spectrum, specifically the visible light band. This shift has led to the discovery of a potential and favorable wireless communication technique commonly referred to as VLC.
VLC constitutes optical links, which enable visible light sources to be employed for transmission of data using air as the transmission medium. VLC technology uses visible light part of the light spectrum. It uses wavelength range from 380 nm to 750 nm (i.e. frequency range from 430 THz to 790 THz) for communication.
For indoor application, the idea is that the existing illuminating devices are utilized to transmit data using the same energy which is being used for illumination. VLC is considered to be a medium-range communication technique. This is by virtue of propagation distance which is limited by the luminaries which in most cases are white light-emitting diodes (WLEDs).
Visible Light Communication (VLC) technology:
- The Visible Light Communication (VLC) technology uses light instead of radio frequency signals to transmit the data.
- The VLC technology uses the visible light spectrum (380 to 750 nanometers) to transmit data across a wireless network of communication.
- VLC-based networks can be used to provide fast, and highly stable internet connections in smaller coverage zones of offices and homes.
- The objective of VLC is to increase data rates in wireless communication and to have better performance of networks especially for indoor networks using light emitting diode (LED), lamps.
- LiFi or light fidelity is a subtype of VLC technology that uses light waves in the visible/invisible/infrared spectrum to transmit data. Harald Haas first introduced it in his 2011.
- Bluetooth has a transfer rate of up to 2.1 Mbps, while Lifi has the data transmission rate up to 224 Gbps.
A comparison between VLC and RF technologies
- VLC offers a wireless communication service with an enormous bandwidth capable of transmitting at very high data rates. The VLC bandwidth is approximately ten thousand folds that of the entire RF bandwidth.
- The luminaires used for VLC systems are energy efficient as they use less power despite their high light intensity, and they also come at a very low cost.
- The VLC systems are much safer compared to RF systems in the sense that there are minimal or no medical health complications caused by visible light. Emissions from RF equipment and devices may be harmful to humans and medical equipment if the radiation power exceeds a particular measure.
- In VLC systems, there is no requirement for sophisticated antennas to transmit data from the light source through the air.
- One more factor that makes VLC systems attractive over RF systems is that they have intrinsic security. The control of transmitted data in the physical layer is simple as communication is commonly in line of sight (LoS). This avoids invasion of the communication system by passive eavesdroppers.
- In contrast to RF, visible light is not capable of penetrating solid surfaces such as walls. The incapability of wall penetration enables the creation of small cells to transmit without interference between cell locations (i.e., intercell interference).
- RF communications are prone to problems, such as lack of spectrum resources, electromagnetic interference , VLC employs the unlicensed frequency spectrum resources at 400–800 THz , which can provide a high data transmission rate and a strong resistance to electromagnetic interferences
- Dueto its appealing advantages, including abundant and unregulated spectrum resources, no electromagnetic interference (EMI) radiation and high security, visible light communication (VLC) using light-emitting diodes (LEDs) or laser diodes (LDs) has been envisioned as one of the key enabling technologies for 6G and Internet of Things (IoT) systems.
Hence, statement 2 is incorrect and 1, 3 and 4 are correct.
4. With reference to “Blockchain Technology” consider the following statements:
1. It is a public ledger that everyone can inspect but which no single user controls.
2. The structure and design of the blockchain is such that all the data in it are about cryptocurrency only.
3. Applications that depend on the basic features of blockchain can be developed without anybody’s permission.
Which of the statements given above is/are correct?
(a) 1 only
(b) 1 and 2 only
(c) 2 only
(d) 1 and 3 only
4. Ans: d
Explanation:
Blockchain is a shared, immutable ledger that facilitates the process of recording transactions and tracking assets in a business network.
An asset can be tangible (a house, car, cash, land) or intangible (intellectual property, patents, copyrights, branding). Virtually anything of value can be tracked and traded on a blockchain network, reducing risk and cutting costs for all involved.
Bitcoin is an unregulated, digital currency. Bitcoin uses blockchain technology as its transaction ledger.
Hence, statement 2 is incorrect.
Blockchain is ideal for delivering that information because it provides immediate, shared, and observable information that is stored on an immutable ledger that only permissioned network members can access. A blockchain network can track orders, payments, accounts, production and much more. And because members share a single view of the truth, you can see all details of a transaction end to end, giving you greater confidence, and new efficiencies and opportunities.
Key elements of a blockchain
Distributed ledger technology All network participants have access to the distributed ledger and its immutable record of transactions. With this shared ledger, transactions are recorded only once, eliminating the duplication of effort that’s typical of traditional business networks.
Immutable records
No participant can change or tamper with a transaction after it’s been recorded to the shared ledger. If a transaction record includes an error, a new transaction must be added to reverse the error, and both transactions are then visible.
Smart contracts
To speed transactions, a set of rules that are called a smart contract is stored on the blockchain and run automatically. A smart contract defines conditions for corporate bond transfers, include terms for travel insurance to be paid and much more.
Hence, statement 1 is correct.
How blockchain works
- As each transaction occurs, it is recorded as a “block” of data
- Those transactions show the movement of an asset that can be tangible (a product) or intangible (intellectual).
- The data block can record the information of your choice: who, what, when, where, how much. It can even record the condition, such as the temperature of a food shipment.
- Each block is connected to the ones before and after it
- These blocks form a chain of data as an asset moves from place to place or ownership changes hands.
- The blocks confirm the exact time and sequence of transactions, and the blocks link securely together to prevent any block from being altered or a block being inserted between two existing blocks.
- Transactions are blocked together in an irreversible chain: a blockchain
- Each additional block strengthens the verification of the previous block and hence the entire blockchain. Rendering the blockchain tamper-evident, delivering the key strength of immutability. Removing the possibility of tampering by a malicious actor, and builds a ledger of transactions you and other network members can trust.
Benefits of blockchain
Greater trust
With blockchain, as a member of a members-only network, you can rest assured that you are receiving accurate and timely data. And that your confidential blockchain records are shared only with network members to whom you granted access.
Greater security
Consensus on data accuracy is required from all network members, and all validated transactions are immutable because they are recorded permanently. No one, not even a system administrator, can delete a transaction.
More efficiencies
With a distributed ledger that is shared among members of a network, time-wasting record reconciliations are eliminated. And to speed transactions, a set of rules that are called a smart contract can be stored on the blockchain and run automatically.
Many blockchains are entirely open source. This means that everyone can view its code. This gives auditors the ability to review. However, it also means there is no real authority on who controls the source code or how it is edited. Because of this, anyone can suggest changes or upgrades to the system.
Hence, statement 3 is correct.
5. When reference to carbon nanotubes, consider the following statements:
1. They can be used as carriers of drugs and antigens in the human body.
2. They can be made into artificial blood capillaries for an injured part of the human body.
3. They can be used in biochemical sensors.
4. Carbon nanotubes are biodegradable.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2, 3 and 4 only
(c) 1, 3 and 4 only
(d) 1, 2, 3 and 4
5. Ans: c
Explanation:
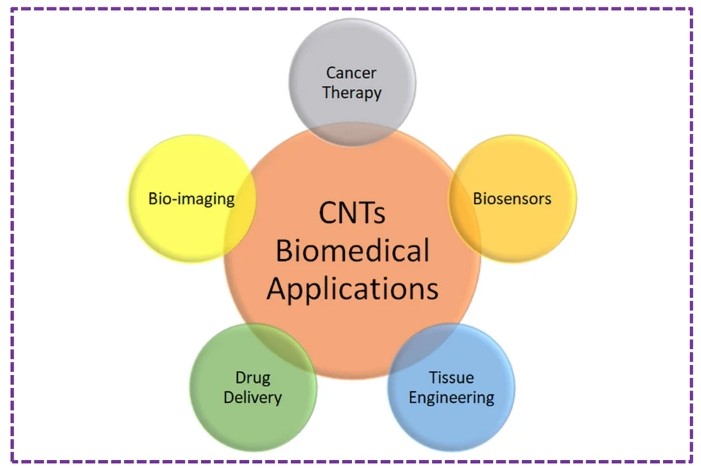
Carbon nanotubes (CNTs) are carbon-based nanomaterials with a tubular structure composed of rolled up graphene sheets. These tubes can consist of single or multiple graphene layers. CNTs share the same π-bond character as graphene, allowing electrons to be delocalized throughout the structure.
Carbon Nanotubes Uses and Applications
- Automotive parts
- Electronics: circuitry, batteries, supercapacitors
- Photovoltaic technology – including solar panels, LEDs, sensors, transistors, field emitting devices, fuel cells, actuators (devices that power physical movement)
- Absorbents
- Catalysts
- Biomedicine: drug delivery, biosensing, bioimaging, nanorobotics, gene therapy and tissue regeneration (Biosensors are devices used to detect the presence or concentration of a biological analyte, such as a biomolecule, a biological structure or a microorganism.)
- Agriculture: bioremediation, water purification
- Carbon nanotubes can be added to a material or substance (nanocomposite) to enhance strength. This is useful, for example, in the manufacture of sportswear, or materials used in the deflection of projectiles including bullet-proof vests.
The greatest concern about the risk of CNTs is related to their unique physicochemical nature: specifically, these materials are extremely stable and difficult to degrade. Historically, it was widely accepted that CNTs could only be chemically degraded by strong oxidants or heat treatment in oxygen .In 2008, however, a pioneering study showed for the first time that CNTs could be biodegraded through enzymatic oxidation by horseradish peroxidase (HRP).
Capillary blood vessels are minute blood vessels, 5–10 μm in diameter, carrying blood from arterioles to venules.The capillaries are very thin and form a fine network called a capillary bed.
Limitations with carbon nanotubes
An important discovery has been made about the safety issues of using carbon nanotubes as biomaterials which come into contact with blood. When blood comes into contact with foreign surfaces the blood’s platelets are activated which in turn leads to blood clots being formed. They found that the carbon nanotubes did actually stimulate blood platelet activation, subsequently leading to serious and devastating blood clotting.
This can be catastrophic in clinical settings.
Hence, option c is correct.
6. Consider the following activities:
1. Spraying pesticides on a crop field
2. Inspecting the craters of active volcanoes
3. Collecting breath samples from spouting whales for DNA analysis.
At the present level of technology, which of the above activities can be successfully carried out by using drones?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
6. Ans: d
Explanation:
Drones can be used to spray chemicals like fertilizers, pesticides, etc. based on the spatial variability of the crops and field. The amount of chemicals to be sprayed can be adjusted depending upon the crop conditions, or the degree of severity of the insect-pest attack. In this way, drones pave the pathway to precision agriculture.
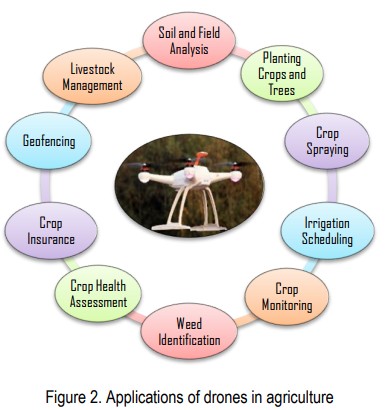
A drone, or unmanned aerial vehicle (UAV), is a remote-controlled device that allows a pilot to remain a safe distance from an active crater while the drone is maneuvered to the site of interest. Drones can be piloted manually or with an autonomous navigation system. Compact gas sensors can be mounted onto the drone that take measurements while the drone is in the air.
The concentrations of carbon dioxide (CO2), sulfur dioxide (SO2), and hydrogen sulfide (H2S) can be measured by flying the drone right into the plume of gas as it emerges from the volcano.
The breath samples provided scientists with DNA and hormone and bacteria measurements. The breath samples provided scientists with DNA and hormone and bacteria measurements
Hence, statements 1, 2, 3 are correct.
7. The experiment will employ a trio of spacecraft flying in formation in the shape of an equilateral triangle that has sides one million kilometers long, with lasers shining between the craft. The experiment in question refers to
(a) Voyager-2
(b) New Horizons
(c) LISA Pathfinder
(d) Evolved LISA
7. Ans: d
Explanation:
The evolved Laser Interfermoter Space Antenna (eLISA) is a mission aiming at exploring the Gravitational Universe from space for the first time. It involves scientists from eight European countries ‒ Denmark, France, Germany, Italy, The Netherlands, Spain, Switzerland, and the UK ‒ as well as the support of several US-based ones.
The eLISA mission consists of a “Mother” and two “Daughter” spacecrafts. These will orbit the Sun in a triangular configuration. The three satellites will form a precision interferometer, with the two Daughter spacecrafts connected to the Mother one by 1 million km long laser beams. This interferometer will be capable of detecting gravitational waves at frequencies in the range of 0.1 mHz to 1 Hz. Such a frequency interval is not accessible on Earth due to arm length limitations and to noise caused by the terrestrial gravity gradient noise: in this sense, eLISA will complement the efforts of ground-based gravitational-wave detectors.
What are Gravitational Waves?
A gravitational wave is an invisible (yet incredibly fast) ripple in space.
More than 100 years ago,Albert Einstein came up with many ideas about gravity and space.
Einstein predicted that something special happens when two bodies—such as planets or stars—orbit each other. He believed that this kind of movement could cause ripples in space. These ripples would spread out like the ripples in a pond when a stone is tossed in. Scientists call these ripples of space gravitational waves.
Gravitational waves are invisible. However, they are incredibly fast. They travel at the speed of light (186,000 miles per second). Gravitational waves squeeze and stretch anything in their path as they pass by.
What causes gravitational waves?
The most powerful gravitational waves are created when objects move at very high speeds. Some examples of events that could cause a gravitational wave are:
- when a star explodes asymmetrically (called a supernova)
- when two big stars orbit each other
- when two black holes orbit each other and merge
But these types of objects that create gravitational waves are far away. And sometimes, these events only cause small, weak gravitational waves. The waves are then very weak by the time they reach Earth. This makes gravitational waves hard to detect.
How do we know that gravitational waves exist?
In 2015, scientists detected gravitational waves for the very first time. They used a very sensitive instrument called LIGO (Laser Interferometer Gravitational-Wave Observatory). These first gravitational waves happened when two black holes crashed into one another. The collision happened 1.3 billion years ago. But, the ripples didn’t make it to Earth until 2015!
What do Gravitational Waves tell us?
Gravitational waves are a powerful new probe of the Universe that uses gravity instead of light to take measure of dynamical astrophysical phenomena. Studying gravitational waves gives enormous potential for discovering the parts of the universe that are invisible by other means, such as black holes, the Big Bang, and other, as yet unknown, objects.
LISA (Laser Interferometer Space Antenna) Pathfinder
ESA’s (European Space Agency) LISA (Laser Interferometer Space Antenna) Pathfinder spacecraft demonstrated technologies required for LISA, a future space probe designed to detect ripples in space-time called gravitational waves.
Hence, option d is correct.
8. Consider the following statements:
1. Genetic changes can be introduced in the cells that produce eggs or sperms of a prospective parent.
2. A person’s genome can be edited before birth at the early embryonic stage.
3. Human induced pluripotent stem cells can be injected into the embryo of a pig.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 and 3 only
(c) 2 only
(d) 1, 2 and 3
8. Ans: d
Explanation:
Gene editing is a type of gene therapy that removes, disrupts, alters, or corrects faulty elements of DNA within a gene of interest. Gene editing uses technology designed to make targeted changes inside the cell.
Somatic gene therapy and germ line gene therapy
Gene therapy can be divided into somatic gene therapy and germ line gene therapy, depending on the cells in which the genetic material is altered
Somatic cells are the cells which make up the vast majority of tissues in the body except for sex cells (eggs and sperm). In the case of somatic gene therapy the genetic material of human cells are altered. Such alterations cannot be genetically transferred.
Reproductive cells, known as germline cells or germ cells, are those sex cells (eggs and sperm) that pass on genes from parents to their children.
Our reproductive cells, known as germline cells or germ cells, are those sex cells (eggs and sperm) that pass on genes from parents to their children. Germline gene editing involves altering the specific genes of an egg, sperm cell, or early embryo (i.e., up to five days after fertilization) in a laboratory dish. Germline gene editing removes, disrupts, alters, or corrects faulty elements of DNA within a gene in sex cells.
In the case of germ line gene therapy the genetic material of gametes are altered. The alterations are transferred to the offspring and are therefore genetically transferred.
Hence, statements 1 & 2 are correct.
Embryo editing
Early embryos only have a few cells, so the number of targeted cells for editing would be much smaller. As the embryo develops, those few edited cells would divide, and divide again, and could theoretically result in the birth of a child with many cells having the desired edit.
An alternative to the embryo editing approach would be to edit the germ cells (egg or sperm) of one of the parents with the goal of then using in vitro fertilization (IVF) to create a fertilized embryo that has the desired genetic change
Clinical use of germline gene editing is prohibited in the United States, Europe, the United Kingdom, China, and many other countries around the world.
Embryonic stem cells (ESCs).
These are pluripotent stem cells derived from embryos. As ESCs are pluripotent they retain the ability to self-renew and to form any cell in the body. ESCs have the advantage of versatility due to their pluripotency, but the use of embryos in the development of therapeutic strategies raises some ethical concerns.
In addition, stem cell lines generated from embryos are not genetically matched to the patient which can increase the chance that the transplanted cell is rejected by the patient’s immune system.
Human stem cells can integrate into developing pig embryos, a finding that could lead to new ways of growing human organs and studying early human development.
Human and pig pluripotent stem cells have emerged as promising tools in regenerative medicine. Compared to mice, pigs offer a more relevant animal model due to their genetic and physiological similarities to humans.
In addition, the integration of human PSCs into pig embryos and the use of pig PSCs for generating humanized pig organs through blastocyst complementation or blastoid formation have opened up new avenues for organ transplantation.
Hence, statement 3 is correct.
9. What is the importance of using Pneumococcal Conjugate Vaccines in India?
1. These vaccines are effective against pneumonia as well as meningitis and sepsis.
2. Dependence on antibiotics that are not effective against drug-resistant bacteria can be reduced.
3. These vaccines have no side effects and cause no allergic reactions.
Select the correct answer using the code given below:
(a) 1 only
(b) 1 and 2 only
(c) 3 only
(d) 1, 2 and 3
9. Ans: b
Explanation:
A vaccine is a biological preparation that improves immunity to a specific disease. It typically contains an agent that resembles a disease-causing microorganism and is often made from weakened or killed forms of the microbe. The agent stimulates the body’s immune system to recognize the agent as foreign, destroy it, and “remember” it so that the immune system can more easily recognize and destroy any of these microorganisms that it later encounters.
vaccines are administered prior to infection. Their role is to prime the immune system to fight any future infections, so that they can be brought under control before the disease-causing microorganism have had a chance to multiply.
Vaccines are of different types – killed Vaccines, attenuated Vaccines, toxoid Vaccines, subunit Vaccines, Conjugate Vaccines, experimental Vaccines , Valence Vaccines
| Conjugate VaccinesCertain bacteria have polysaccharide outer coats that are poorly immunogenic. By linking these outer coats to proteins (such as toxins), the immune system can be led to recognize the polysaccharide as if it were a protein antigen. Conjugate vaccines are better suitable where the polysaccharide outer coats of bacteria are poorly immunogenic. |
Pneumococcal conjugate vaccine
Pneumococcal conjugate vaccine can prevent pneumococcal disease.
Pneumococcal disease refers to any illness caused by pneumococcal bacteria.
- These bacteria can cause many types of illnesses, including pneumonia, which is an infection of the lungs.
- Pneumococcal bacteria are one of the most common causes of pneumonia.
- Besides pneumonia, pneumococcal bacteria can also cause: Ear infections Sinus infections Meningitis (infection of the tissue covering the brain and spinal cord) Bacteremia (infection of the blood), Sepsis (a life-threatening reaction to an infection, Infection prevention is the only way to prevent sepsis)
An important way to reduce the risk of contracting infections is by receiving vaccinations that target certain illnesses.
Most pneumococcal infections are mild. However, some can result in long-term problems, such as brain damage or hearing loss. Meningitis, bacteremia, and pneumonia caused by pneumococcal disease can be fatal.
| Sepsis is a life-threatening medical emergency caused by your body’s overwhelming response to an infection. Without urgent treatment, it can lead to tissue damage, organ failure and death.Bacterial infections are one of the most common causes of sepsis. Fungal, parasitic and viral infections are also potential sepsis causes. |
Hence, statement 1 is correct.
Risks of Pneumococcal conjugate vaccine reaction – Redness, swelling, pain, or tenderness where the shot is given, and fever, loss of appetite, fussiness (irritability), feeling tired, headache, muscle aches, joint pain, and chills can happen after pneumococcal conjugate vaccination.
Hence, statement 3 is incorrect.
Vaccines for Antimicrobial Resistance (AMR)
Antimicrobial resistance (AMR) threatens the effective prevention and treatment of an ever-increasing range of infections caused by bacteria, parasites, viruses and fungi.
AMR occurs when bacteria, viruses, fungi or parasites change over time and no longer respond to medicines making infections harder to treat and increasing the risk of disease spread, severe illness and death. As a result, the medicines become ineffective and infections persist in the body, increasing the risk of spread to others.
vaccines are administered prior to infection. Their role is to prime the immune system to fight any future infections, so that they can be brought under control before the bacteria have had a chance to multiply.
Vaccination can help to combat overuse by preventing infections that would otherwise require antibiotic treatment and help curb the spread of resistant strains.
Vaccines are an essential tool as part of a holistic response to reduce AMR. They prevent both drug-sensitive and drug-resistant infections, reduce the use and overuse of antimicrobials, and slow the emergence and spread of drug-resistant pathogens.
Hence, statement 2 is correct.
10. In India, the term “Public Key Infrastructure” is used in the context of:
(a) Digital security infrastructure
(b) Food security infrastructure
(c) Health care and education infrastructure
(d) Telecommunication and transportation infrastructure
10. Ans: d
Explanation:
Public key infrastructure (PKI) is a comprehensive framework for assigning, identifying and verifying user identity through digital certificates used for enabling trustworthy and secure digital communications.
Paired with public-key cryptography, digital certificates act as virtual passports—authenticating the identity and permissions of various users and entities when establishing secure end-to-end communication over public or private networks. Encompassing elements of software, hardware, policies and procedures, PKI formalizes the process to create, distribute, manage and revoke digital certificates.
Public key infrastructure (PKI) provides protocols to validate the authenticity of the digital certificates that underscore the trust in public key cryptography systems. A cornerstone of cybersecurity, cryptography provides confidentiality, integrity, nonrepudiation and authenticity. PKI adds validity to cryptographic systems by cryptographically binding digital certificates to unique users, institutions, entities and third parties.
The ability to establish the secure transfer of information between users, entities and devices enables ecommerce and banking platforms to collect financial information, allows Internet of Things (IoT) connected devices and establishes confidential lines of communication, for secure email web servers, cybersecurity specialists rely on data encryption to securely encrypt (scramble) and decrypt (unscramble) sensitive data.
The two primary types of data encryption are known as public key cryptography and private key cryptography.
What is public key cryptography?
Also known as asymmetric encryption or public key encryption, public key cryptography uses a pair of keys, a shared public key and a private key that is unique to each party. The public key is used for encryption while the private key is used for decryption.
What is private key cryptography?
Also known as symmetrical or secret key cryptography, private key cryptosystems use only one key for both encryption and decryption.
Cryptography is also used for common messaging applications like email and WhatsApp to provide end-to-end encryption (E2EE) and maintain the privacy of users’ conversations. With E2EE, only the sender and intended recipient can decrypt and read their messages, making it nearly impossible for third parties—including users’ own service providers—to access the content.
While symmetric cryptography is faster, asymmetric cryptography is often more practical and secure. In practice, both types of cryptosystems are often used together.
However, both types of systems can be vulnerable to so-called man-in-the-middle (MitM) attacks, in which a malicious eavesdropper might intercept secure data during transmission.
Hence, option d is correct.
11. Which of the following statements are correct regarding the general difference between plant and animal cells?
1. Plant cells have cellulose cell walls whilst animal cells do not.
2. Plant cells do not have plasma membranes, unlike animal cells which do.
3. Mature plant cell has one large vacuole whilst animal cell has many small vacuoles.
Select the correct answer using the code given below:
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
11. Ans: c
Explanation:
Cells is the fundamental, structural and functional unit of life. All the plants and animals are made of cells. Some forms of life, however, are made of only a single cell, such as the many species of bacteria and protozoa. Cells, whether living on their own or as part of a multicellular organism, are usually too small to be seen without a light microscope.
All cells are surrounded by a structure called the cell membrane — which, much like the walls of a house, serves as a clear boundary between the cell’s internal and external environments. The cell membrane is sometimes also referred to as the plasma membrane.
Plant cells have certain distinguishing features, including chloroplasts, cell walls, and intracellular vacuoles. Photosynthesis takes place in chloroplasts; cell walls allow plants to have strong, upright structures; and vacuoles help regulate how cells handle water and storage of other molecules.
PLASMA MEMBRANE OR CELL MEMBRANE :
- This is the outermost covering of the cell that separates the contents of the cell from its external environment. The plasma membrane allows or permits the entry and exit of some materials in and out of the cell. It also prevents movement of some other materials.
- The cell membrane, therefore, is called a selectively permeable membrane. It is found in both plant and animals cells.
- The plasma membrane is flexible and is made up of organic molecules called lipids and proteins. However, we can observe the structure of the plasma membrane only through an electron microscope.
- The flexibility of the cell membrane also enables the cell to engulf in food and other material from its external environment. Such processes are known as endocytosis. Amoeba acquires its food through such processes.
Hence, statement 2 is incorrect.
Cell Wall:
- Plant, fungi and bacteria, in addition to the plasma membrane in their cell, have another rigid outer covering called the cell wall. The cell wall lies outside the plasma membrane. The plant cell wall is mainly composed of cellulose. Cellulose is a complex substance and provides structural strength to plants.
- Cell walls permit the cells of plants, fungi and bacteria to withstand very dilute (hypotonic) external media without bursting. In such media the cells tend to take up water by osmosis. Because of their walls, such cells can withstand much greater changes in the surrounding medium than animal cells.
Hence, statement 1 is correct.
Vacuoles
- Vacoules are storage sacs for solid or liquid contents. Vacuoles are small sized in animal cells while plant cells have very large vacuoles. The central vacuole of some plant cells may occupy 50-90% of the cell volume. Most mature plant cells have a large central vacuole that helps to maintain the turgidity of the cell and stores important substances including wastes. Plant cells use vacuoles to adjust their size and turgor pressure. Vacuoles usually account for changes in cell size when the cytoplasmic volume stays constant.
Hence, statement 3 is correct.
12. In India, why are some nuclear reactors kept under “ IAEA Safeguards” while others are not?
(a) Some use uranium and others use thorium
(b) Some use imported uranium and others use domestic supplies.
(c) Some are operated by foreign enterprises and others are operated by domestic enterprises
(d) Some are State-owned and others are privately-owned
12. Ans: b
Explanation:
Safeguards are a main plank in the global nuclear security regime because they allow the IAEA to make sure that nuclear materials like uranium and plutonium in the civil power sector are never used in military programs.
An Agreement between the Government of India and the IAEA for the Application of Safeguards to Civilian Nuclear Facilities (nuclear safeguards agreement ) was signed in 2009.
Under this agreement India will decide on the reactors to be placed under IAEA safeguards only after assessing if these will be fuelled by uranium procured from abroad.
By placing the reactors under the IAEA safeguards, India gives the international nuclear energy watchdog access to them. This step was taken by the country in 2014 to demonstrate that its nuclear energy programme was for peaceful purposes.
This is a necessary step under the Indo-US nuclear deal.
There are at present 22 operational reactors in India, of which 14 are under the International Atomic Energy Agency (IAEA) safeguards.
Hence, option b is correct.
13. With reference to solar water pumps, consider the following statements:
1. Solar power can be used for running surface pumps and not for submersible pumps.
2. Solar power can be used for running centrifugal pumps and not the ones with piston.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 only
(c) Both 1 and 2
(d) Neither 1 nor 2
13. Ans: d
Explanation:
A solar water pump is an application of photovoltaic technology which converts solar energy into electricity to run the pumping system thereby, replacing erratic grid supply and pollution-causing diesel-powered versions. The solar water pump is powered by solar modules that helps draw surface or ground water out for irrigation.
Solar power can be used for both DC and AC range of Solar Water Pumps in both Surface and Submersible categories.
Piston Pump and Centrifugal Pump both can be run on solar power that uses electricity generated from a photovoltaic array.
Surface pumps and submersible pumps are two types of pumps used to move fluids from one place to another. While both types of pumps serve the same basic purpose, there are several differences between the two.
- Surface pumps are pumps that are installed on the surface, or above ground, and are used to draw water from a well or other water source. They are often used in residential and commercial applications, such as irrigation, water supply, and fire protection systems. Surface pumps come in a variety of types, including centrifugal pumps, jet pumps, and positive displacement pumps. They rely on atmospheric pressure to lift water.
- On the other hand, submersible pumps are pumps that are designed to be completely submerged in water or other fluids. They are typically used in applications such as groundwater supply, drainage, and sewage pumping. Submersible pumps are often more efficient than surface pumps because they do not have to work as hard to lift water from the source. They also have the advantage of being less noisy than surface pumps.
- Centrifugal pumps operate on the principle of centrifugal force, which is generated by the rapid rotation of an impeller or an enclosed set of vanes within the pump. This rotation creates a low-pressure area at the centre of the impeller that makes liquid to be drawn into the pump. As the fluid moves outward due to centrifugal force, it gains velocity and is discharged from the pump outlet.
- Reciprocating pumps functions by using a back-and-forth or reciprocating motion to transfer fluids. Unlike centrifugal pumps, which rely on rotation, reciprocating pumps utilise a piston, diaphragm or a plunger to displace the fluid in a controlled manner. This reciprocating action creates a pressure differential that draws in the fluid on one stroke and then pushes it out on the return stroke.
Hence, both statements 1 & 2 are incorrect.



